It’s not been long that a certain Pegasus spyware infiltrated nearly every smartphone operating system in the world and left a lot of companies questioning their methods of security.
One of those companies was Apple, the Pegasus spyware easily sneaked into the iOS and collected sensitive data about users and clipped complete devices. Thus, with the new iOS 14.8’s update, Apple has tried its best to obtain protection against Pegasus and similar Spywares.
The News
According to The New York Times, the iOS 14.8 update fixes a significant vulnerability that Apple experts have been working around the clock to remedy. The Citizen Lab notified Apple this week of the availability of a zero-click iMessage vulnerability that affects Apple's image rendering libraries. The exploit, dubbed as FORCEDENTRY, could be able to infect the iPhone, iPad, Apple Watch, or Mac with the Pegasus spyware. It grants access to the microphone and camera in addition to accessing texts as well as phone calls and emails.
FORCEDENTRY was supplied to governments and other groups by the Israeli NSO Group, and The Citizen Lab found it through examining the phone of a Saudi activist. Information was provided directly to Apple on September 7, and Apple took an entire week to address the problem. Based on data from The Citizen Lab, FORCEDENCY will be in use until at least February 2021.
Apple declares this fix as CVE-2021-30860 and describes it as a maliciously created PDF that could result in random code execution.
It's a bit of a surprise that the Pegasus spyware is noteworthy because it evades BlastDoor, which is specific protection for iMessage that Apple introduced in conjunction with the release of iOS 14. BlastDoor is a sandbox-based security system for messages. It was created to stop exploits similar to Pegasus. However, it's still being developed.
Apple has told The New York Times that it will make spyware-blocking features available within this week's iOS 15 software update to help prevent similar attacks in the future.
How vulnerable is Pegasus?
Pegasus spyware can be described as software for surveillance created by Israeli cyber-intelligence firm NSO Group. NSO Group is known for creating sophisticated software and equipment that is sold exclusively to intelligence and law enforcement agencies of government agencies that have been vetted to serve the sole purpose of preserving lives by stopping terror attacks and crimes, as stated by the company.
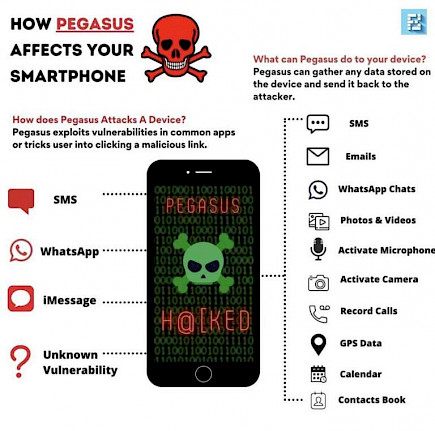
Pegasus is one of these programs which is designed to access your phone without consent, collect sensitive and personal data, and send it to the individual who is monitoring you.
What will it do?
As per Kaspersky, Pegasus spyware can detect the messages sent by the victim's SMS or emails. They can listen in on calls, take screenshots, track keystrokes, and even access the history of contacts and browsing. A different report confirms that hackers can take over the phone's camera and microphone to turn it into a live-streaming surveillance device. It's important to note that Pegasus is a complicated and costly malware specifically designed to monitor those who are of particular interest to them (national delegates, journalists, etc.). Therefore, the typical person is not likely to come across it.
How to detect whether your device is affected or not, using iMazing
To start with the steps to follow so that you can identify the presence of Pegasus spyware on your iPhone, you first require the latest version of iMazing downloaded on the Mac as well as the Windows machine. The spyware detection function is available even to users who are using the trial version of iMazing for free. The software is free and requires a license fee to gain access to all its capabilities.
- After you've installed IMazing 2.14 or a later version on your PC, select Continue Trial when asked to do so to start the trial for the first time.
- Now you can link your iPhone to your PC using the Lightning cable to check for Pegasus spyware.
- You will now find the main options that are available in the trial period on the right. Look through the choices and select Detect Spyware.
- An additional window should be displayed to guide you through the procedure. Click on the Next button to start a spyware detector tool.
- The iMazing application will now prompt you to download the newest Structured Threat Information Expression (STIX) files from the server.
- Once the download is complete, the app will then ask you to make an offline backup of your iPhone data to be used for analysis. It will also prompt you to enable backup encryption. This will protect your backup using a password. It is highly recommended to save your password for later reference.
- iMazing will begin backups of your data. There will be no need to perform any manual tasks on your end since the app will automatically complete the process of backup.
- When the backup process is done, iMazing will decrypt the backup data and look through the files to find any indication of the Pegasus spyware.
- It will then display the results, which will tell you if the spyware was created to harm your device. You will see the number of warnings as well as the total number of logs. It also lets you access the whole report using Excel to examine the warnings.
Winding-up
With the new update, Apple has subdued a lot of negative comments for now. But, what about tomorrow?
Well, for starters. With the iOS 15, Apple has tried its level best to reach a previously unattainable range of security. So, it’s our earnest request to all the users -- Please, update your iOS as soon as possible and use iMazing for any type of file transfer.





