All tools allowing you to jailbreak iOS 13 are closed source, but now thanks to Linus Henze a new open-source jailbreak tool was released to the public. Fugu jailbreak supports all devices with the A10/A10X CPU running on iOS 13 - iOS 13.5.1.
Download Fugu Jailbreak
Changelog
Version 0.4
- This release adds persistence, i.e. your changes to the root file system will be preserved across reboots.
Version 0.3
- This release now has an auto-installer for Sileo, SSH, and Substitute.
- Put your iDevice into DFU mode, run Fugu iStrap, unlock your iDevice, and follow the on-screen prompts.
Version 0.2
- This release adds experimental MobileSubstrate support.
- Currently only works in Sileo and Settings, I'll fix that in v0.3
- Updated for devices with a white boot screen
What is Fugu Jailbreak?
Fugu is an open-source jailbreak tool that supports all devices with the A10/A10X CPU running on iOS 13 - 13.5.1. The jailbreak will install Sileo, SSH, and Substitute automatically. Additionally, all changes to the root file system are now persistent. Fugu is based on the checkm8 exploit and was tested on iPad Pro and iPhone 7.
checkm8 is a powerful open-source exploit to jailbreak many iOS devices that is used also by checkra1n jailbreak. It uses a permanent unpatchable bootrom exploit that is not compatible with only the latest devices including iPhone 11 Pro, iPhone 11, iPhone 11 Pro Max, iPhone XR, iPhone XS Max, iPhone XS, and iPhone XS Max.
Fugu is a macOS only terminal application that exploits your iPhone using checkm8 and uploads iStrap, iStrap loader, and iDownload. iStrap loader is a small shellcode that patches iBoot and loads iStrap after iBoot is done. iStrap is the kernel bootstrapper that patches the kernel, injects boot arguments and shellcode into the kernel. The jailbreak tool is designed to work on iOS 13 - iOS 13.5.1.
What's more, Fugu jailbreak contains iDownload, a small application running on your iDevice. It will be installed during boot and launched instead of launchd. Forks itself and runs launchd. The forked copy will listen on Port 1337 (only on 127.0.0.1, use iproxy to connect) and provide a simple bash-like interface.
This jailbreak is currently in development and only meant to be used by developers. Fugu is released under GNU General Public License and everyone interested to see how it works can find the source code via GitHub.
To jailbreak your iPhone or iPad running iOS and iPadOS 13 put your iDevice into DFU mode, run "Fugu iStrap", unlock your iDevice, and follow the instructions.
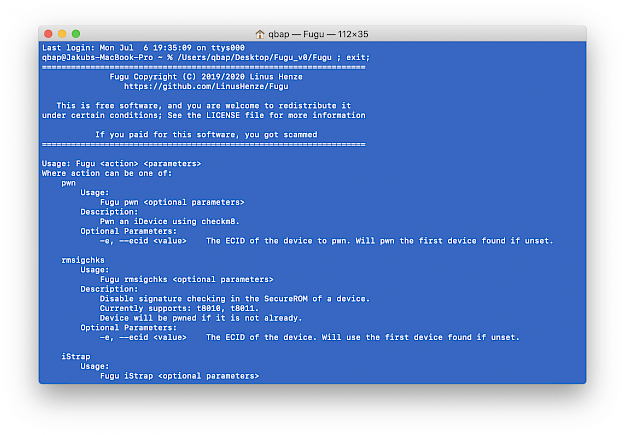
How to use Fugu Jailbreak from terminal
Usage: Fugu <action> <parameters>
Where action can be one of:
pwn
Usage:
Fugu pwn <optional parameters>
Description:
Pwn an iDevice using checkm8.
Optional Parameters:
-e, --ecid <value> The ECID of the device to pwn. Will pwn the first device found if unset.
rmsigchks
Usage:
Fugu rmsigchks <optional parameters>
Description:
Disable signature checking in the SecureROM of a device.
Currently supports: t8010, t8011.
Device will be pwned if it is not already.
Optional Parameters:
-e, --ecid <value> The ECID of the device. Will use the first device found if unset.
iStrap
Usage:
Fugu iStrap <optional parameters>
Description:
Send iStrap to device and boot kernel.
Currently supports: t8010, t8011.
Device will be pwned if it is not already.
Optional Parameters:
--no-install Do not install iDownload. Can only be used if it is currently installed.
Will save ~100 KB of RAM.
Note that iDownload will be deleted when booting without the jailbreak.
--boot-args <value> Set custom boot args.
-e, --ecid <value> The ECID of the device. Will use the first device found if unset.
--restore-fs Restore the root filesystem.
This will NOT rename the filesystem snapshot!
This option disables the jailbreak.
lzss
Usage:
Fugu lzss [input] [output] <optional parameters>
Description:
lzss encode a file so that iBoot will like it.
Required Parameters:
[input <value>] The input file
[output <value>] The output file
Optional Parameters:
--kpp <value> KPP file, will be appended to the data




